Pi-Hole DNS
For this project, I’ve set up a DNS-based filtering tool to block advertisements, tracking and even known malicious sites on my home network.
All through a gadget named after a fruit that’s small enough to fit in my pocket 🍇
Space invaders 👨💻
-
We’ve all slowly succumb to the scourge - personalised ads everywhere you look on the internet.
Whether you’re sympathetic toward the advertising industry or not, by stuffing websites with animations & other data-intensive media we have an objectively slower browsing experience.
In fact, advertising doubles the amount of time it takes to load a webpage on average.
Worse yet is that advertising hosts with large media-intensive ads are slower in serving them to websites because of the number of requests required. Every display ad online goes into an auction with advertising networks that then place bids. Embedded code within them track how well these ads perform with regard to visibility and other metrics.
The Interactive Advertising Bureau has set a guideline of 15 network requests - tops! When in fact, the current average sits around 60.
Unsurprisingly, myself and many others are fed up. So we turn to ad-blockers altogether.
-
I don’t think that I’ve ever told anyone “no” quite as much as I’ve hushed away YouTube premium. Still, 5 second unskippable ads drive me crazy!
Ads mess up our online experience in so many ways. They slow down our browsing time, undermine our privacy & security, break our concentration and adversely affecting our overall attention.
Regular display ads are not only a distraction. They use up valuable screen real estate, break the flow of the page, and suck up bandwidth loading our device with all sorts of cookie-trackers that let strangers spy on what we do online. Going so far as to even load adware that hijacks our browser to inject even crappier ads into our life!
-
So, the kinds of tools that you’d find on the Chrome Store like adblock or ublocker work from within your web browser. They analyse the incoming data sent to your pc when you load a website, then removing or replacing any content that is recognized as an ad.
Now this works great for that one browser, perhaps even that whole computer… but what about ads on devices that don't have or allow ad blocking? Like the advertisements baked into mobile apps, on your smart tv or even on the Google Mobile Discover Page?
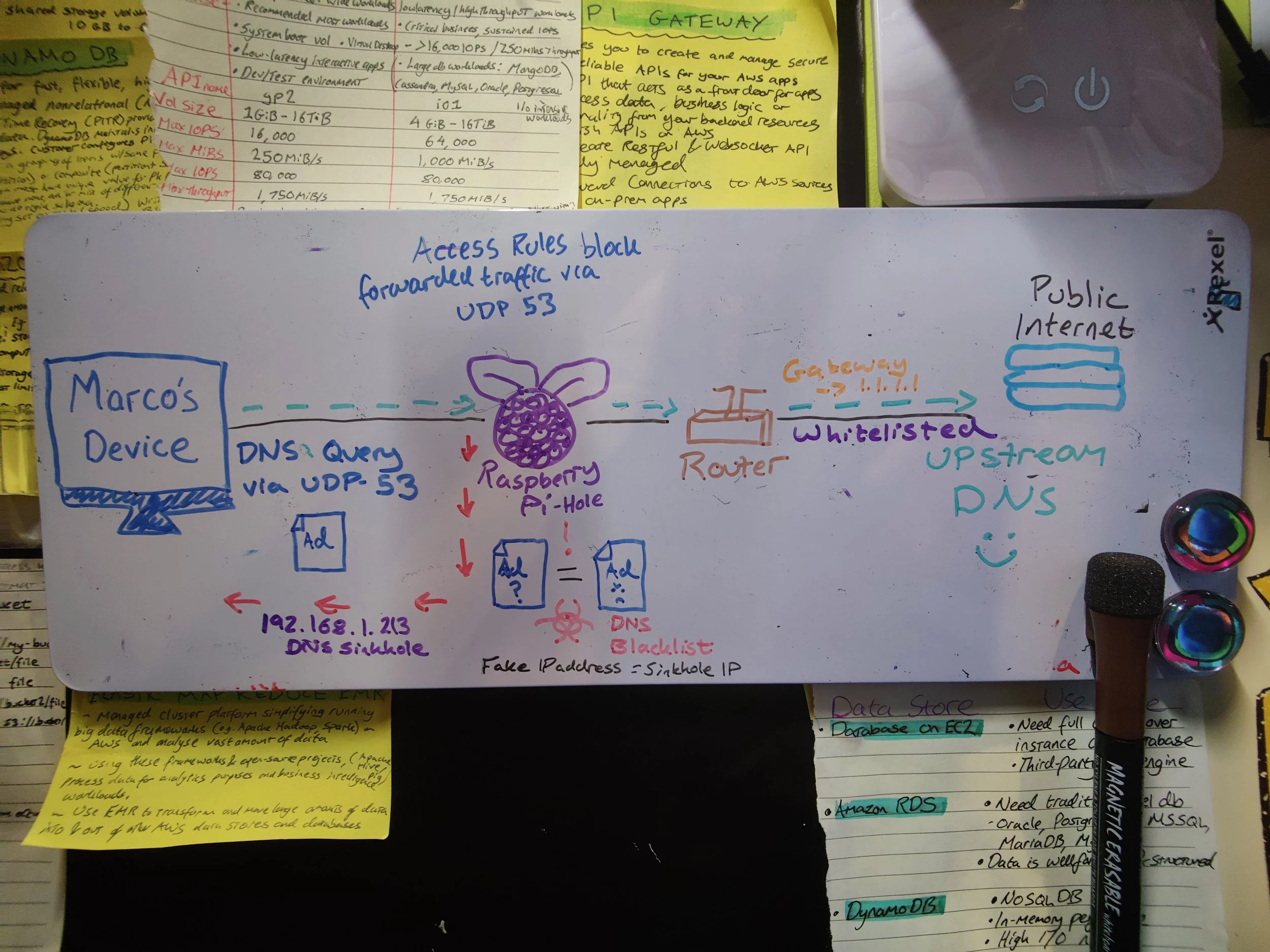
That is where pi-hole comes into play.
-
Let’s say you launch a mobile game on your phone and all the assets required to run it start loading.
We’ve got textures, dialogue, music, etc. At the same time, a request is being made to the URL of the server which manages ads for that app.
Your router’s specified DNS provider then looks up that URL and replies with the IP address of the server so that it can load the ads.Now it’s done this way rather than just baking the ads into the app itself because, among other reasons, it allows advertisers to dynamically serve individually tailored ads even from multiple providers across multiple servers.
What we want then, is a device to stand in-between the DNS provider and our device. Since we can tell that device in the middle a blacklist to drop the requested URL rather than forwarding the request along to the usual DNS provider and subsequently connecting to you to whatever’s on the other side - in this case, an ad server.
Instead, the device will stop the request in its tracks and replies with an unspecified address - essentially telling the device that hey sorry, this ad server doesn’t exist. Oh what a shame, maybe next time.
So now you get the drift. We want a device to redirect our unwanted queries to point them into space. Hence, a DNS sinkhole.
-
And depending on how the device’s ad code handles errors, you’ll either be left with no ad, or a hollowed out box where the ad should be.
And another cool benefit is that if you can blacklist adverts…then this can be applied to practically anything like blocking known tracking services, preventing malicious sites or malware from talking to their controlling server. Even blocking you from downloading Steam onto your work laptop! (Although when there’s a will, there’s a way 😉)
-
Well it isn’t.
You’ll need a few things to complete the set-up, but once all is said & done then the benefits far outweigh the headache.
-
Most ads are served by advertising networks through third-party domains. Their army of trackers pay attention to your behaviour to gradually build a detailed profile on you.
That being said, it isn’t really about you, per se, but instead a bunch of yous that repeat certain behaviours time and time again until it becomes a trend, to then target that trend.
If you’re on Chrome and into the macabre, then click into your profile > privacy & personalisation > Ad personalisation > Full settings > Scroll down > Gasp at the list of attributes which Google have predicted about you.
Although I’m age 26, Google believes that I’m on the cusp of Karenhood sitting somewhere within the 35-64 year old window. But to be fair, I checked my ad profile using my work email account which I’m a little boring with.
But it contains personal information like your age, location, the identities of your family and friends, what you like to look at online, and who knows what else. Any bit of info that they can glean that might be useful will end up in that profile.
Why go to all the trouble to learn so much about you? So they can stick ads in front of you that they think will persuade you to buy their stuff. Or so they can sell the information to the highest bidder.
Online ads aren’t simply ads. They’re actually surveillance tools that strangers use to abuse your privacy.
-
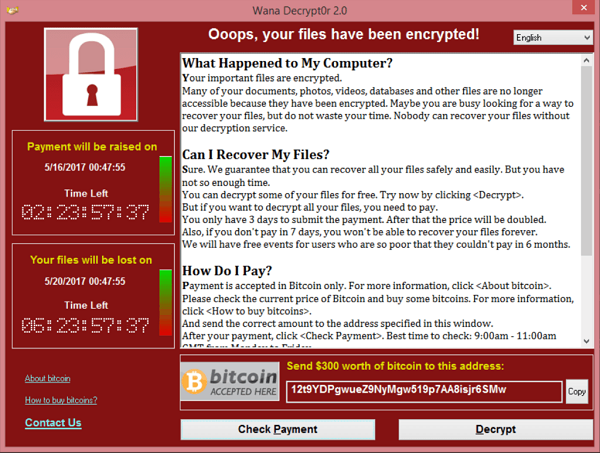
Did you know that it is possible for your device to be infected with malware simply by visiting a website with ads?
Malvertising is the term for spreading malware through infected ads. It works like this: you visit the website. The website loads the infected ads. The infected ads silently, automatically, load the malware onto your device while you are wondering why this page is showing you all these ads for “get rich quick” schemes or whatever.
Most memorable is the wannacry ransomware attack in which infected ads hit users, redirecting the page to servers hosting the malware which broadcast the Angler exploit kit. The kit attempts to find any backdoor into your computer, where it’ll then install cryptolocker-style software, encrypting your hard drive and demanding payment in bitcoin for the keys to unlock it. With no guarantee that it’ll work either.
This stuff really is evil. Even worse, malvertising affects major sites that are presumably secure. Wannacry was hosted on “secure” sites such as the New York Times and BBC.
-
As you might imagine, all those ads running in the background can hurt a site’s performance. Mobile devices are particularly affected. Remember that on your mobile phone, ads appear in the browser, but also hard-baked into many mobile apps. Unwanted ads can have an impact even when you aren’t using a web browser.
Estimates say that mobile ads can use up more than 3/4 of mobile bandwidth and almost half of your mobile data. Mobile networks have gotten faster since then, but surely ads are sucking up more resources too. Notwithstanding the drain upon your phone’s battery life as well.
Ultimately, it doesn’t matter how much of your bandwidth and data ads suck up. It’s we, the uninterested, who are paying for those resources.
In effect, a significant percentage of the money we pay for our data plan goes to pay strangers to put junk on your phone that we don’t even want!
Many internet users find online advertising disruptive, determined to block them altogether.
◀Here are some reasons why ad-blockers have become increasingly important:
But of course, I’m being paid to say all this…If you’d like my actual opinion, then you’ll have to like, subscribe & purchase...
DNS Pi-Hole project
-
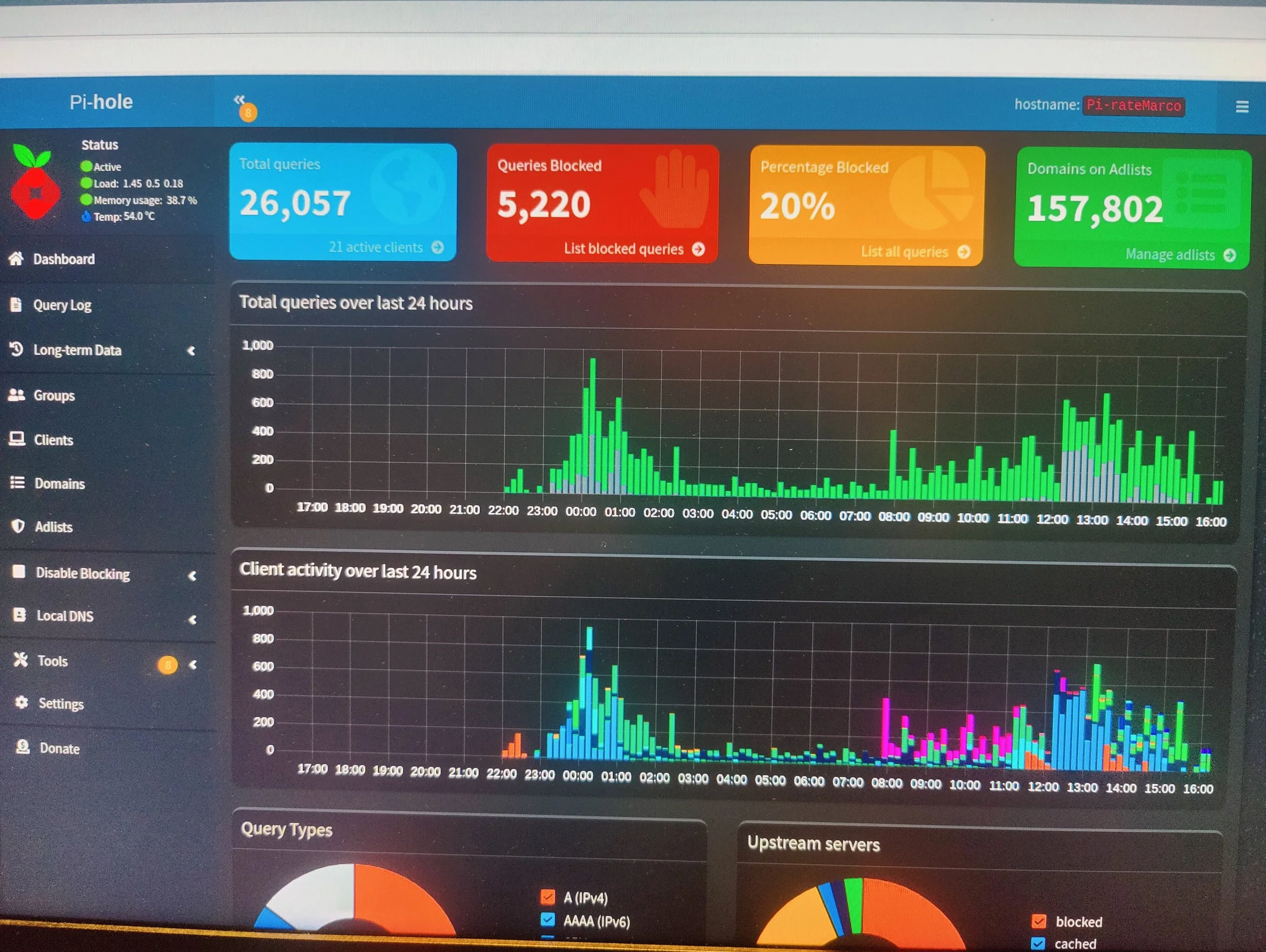
What Pi-hole does is act as my DNS server. Any devices on my home network will connect to it, have certain requests filtered out before venturing out onto the public internet from my home router.
Any DNS requests that match an known ad host will be rejected, meaning the connection will never happen and adverts never load.
Network-wide adblocking is useful for devices which won’t natively allow for adblocking tools - such as my smart TV.
It improves network performance & bandwidth usage because the overall amount of files downloaded during web browsing is reduced.
Moreover, improving security and privacy on my network by avoiding sketchy ad providers.
-
The hardware I used for the set-up:
A Raspberry PI 4 [1.5GHz 64-bit quad-core ARM Cortex-A72 CPU, 1GB LPDDR4 RAM, On-board wireless LAN - dual-band 802.11 b/g/n/ac, Bluetooth 5.0, 2x USB 3.0 ports, 2x USB 2.0 ports & Gigabit ethernet)
A Micro SD card (Only needing ~2Gb for the OS, but I happened to have an 32GB card already. In any case, go big since SD cards are just so cheap nowadays, and space for future projects is always good.)
Power Supply (5.1V 3A USB- power cable)
Sd/uSD Card reader (because my desktop didn’t have one)
Micro HDMI - HDMI cable (optional, but I didn’t want to go headless)
Optional extras which I might get around to…eventually:
Housing for the Raspberry Pi model (nice to keep it protected, but a cardboard egg box also works)
Heat sinks (To keep things nice and cool, also helpful to overclock the Pi)
Perhaps a wireless dongle (to take my Pi-hole with me when I’m on the move and want a personal VPN next time I’m using the public internet at Costa Coffee).
-
Truth be told, I’d been idly jabbing at this project for months now. Raspberry Pi’s supply chains were devastated by the pandemic making it impossible to source any new devices. I was outbid on Ebay 4 times before finally turning to pimoroni.com to buy an overpriced resell. Sucks. But it’s done now.
First, I needed to set up my operating system of choice: Raspbian Buster lite.
Downloaded the Raspberian Buster Lite image from the Raspberry website.
Downloaded and installed balenaEtcher. A reputable uSD card writer/burner.
Flashed the Raspian Buster Lite image onto the uSD card.
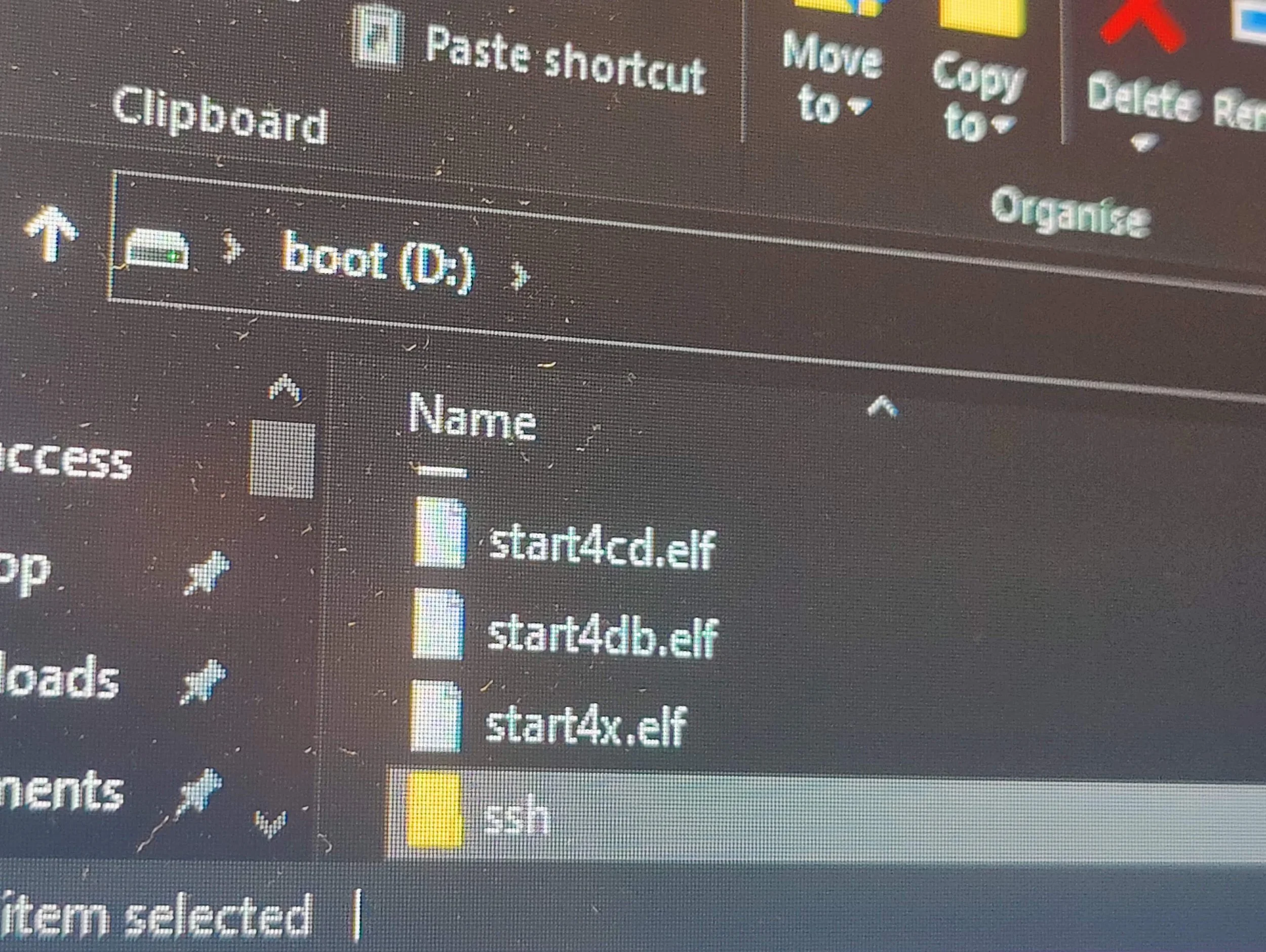
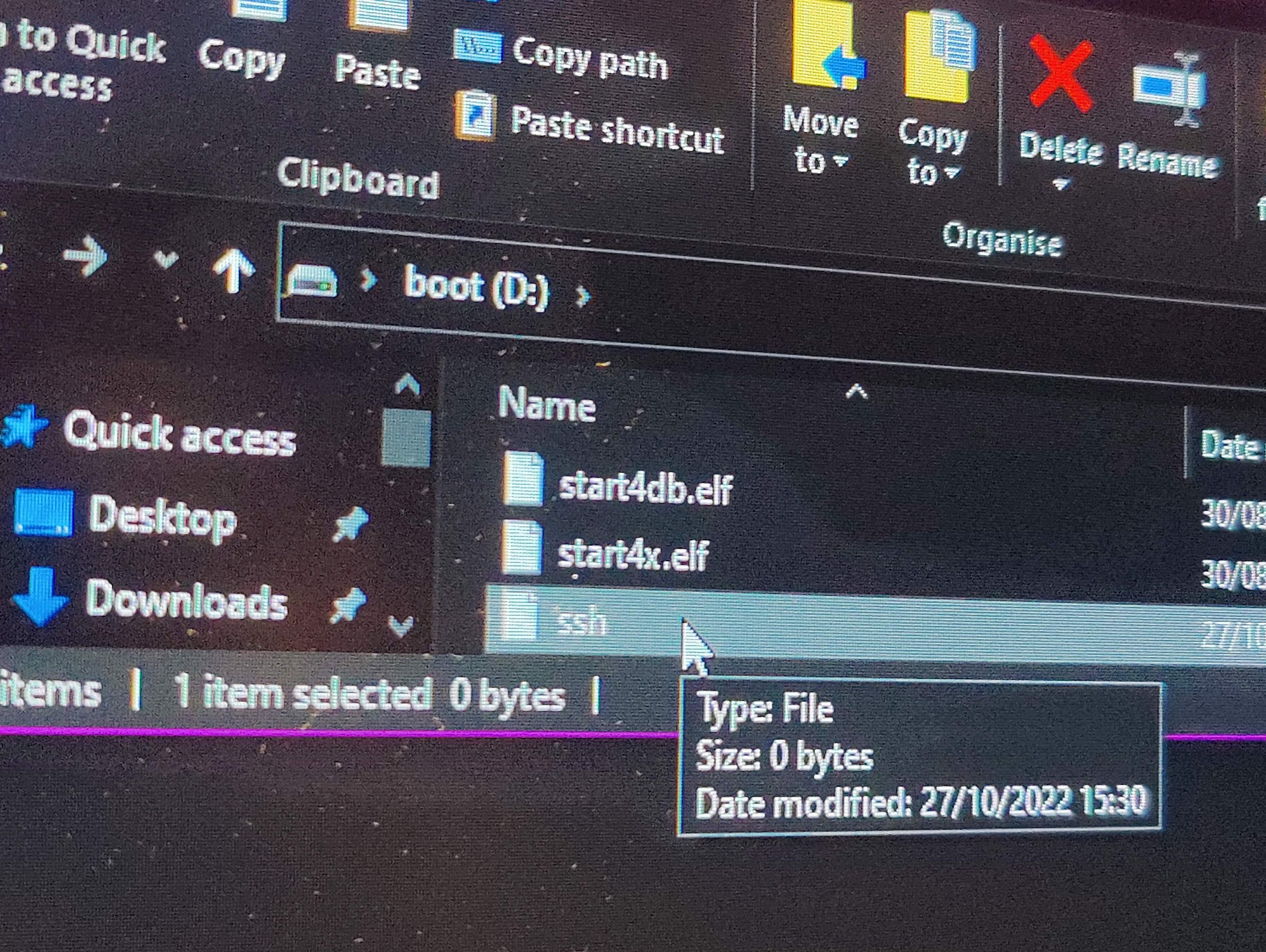
Enabled SSH by creating an extension-less file into the boot partition
Searched for the Raspberry Pi’s IP address so that I could access it over SSH. Using AngryIpScanner to check my home network’s DHCP client/reservation list.
Found the Pi’s IP & MAC address
Assigned it a local Static IP address. Restarted it to allow its new designation.
SSH access via PuTTY to change the default password and update the device (“sudo apt update -y”)
The Raspberry Pi is updated, set with a secure password and ready to install pi-hole!
-
Pi-Hole is the software package that will be handling everything. It sets up and configures a DNS server that can be configured to whitelist and block individual domain names.
Also providing a fancy web frontend with a dashboard to see the stats in real-time and make changes to the overall configuration from a centralised console.
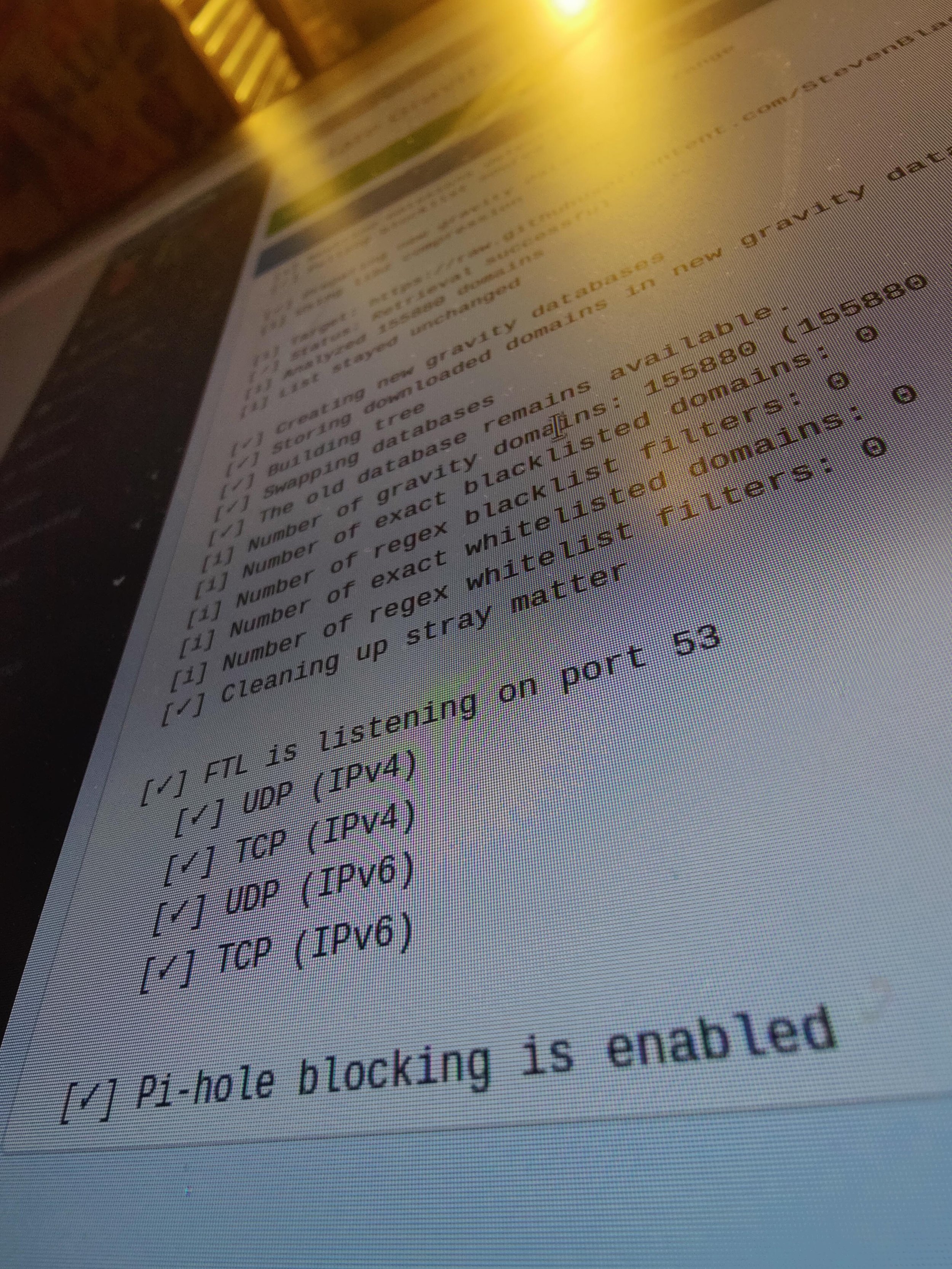
Curled the Pi-hole install script (curl -sSL https://install.pi-hole.net | sudo bash)
Verifed the amount of available free disk space, updating the package list and formatting the uSD card.
Arriving at the “Choose an interface” page, going for the default “eth0” interface for my ethernet cable run in-place at home.
Selected an upstream DNS provider. This is where requests will be forwarded if they’re not blocked by Pi-Hole.
In North West London, Cloudflare DNS is ranked as the top performing public directory, so I chose 1.1.1.1.
Chose the IP4 & IP6 protocols
Confirmed the static IP address of the Pi within my network, making sure there’s no IP conflicts
Had a little panic attack here, since my BT SmartHub6 was fighting back. Limiting my options, it kept reverting the DHCP reservation pool to avoid the static IP address I wanted. Eventually, I found a workaround.
Configured the admin web interface, Lighttpd web server and DNS logging modes.
Installation is now complete!
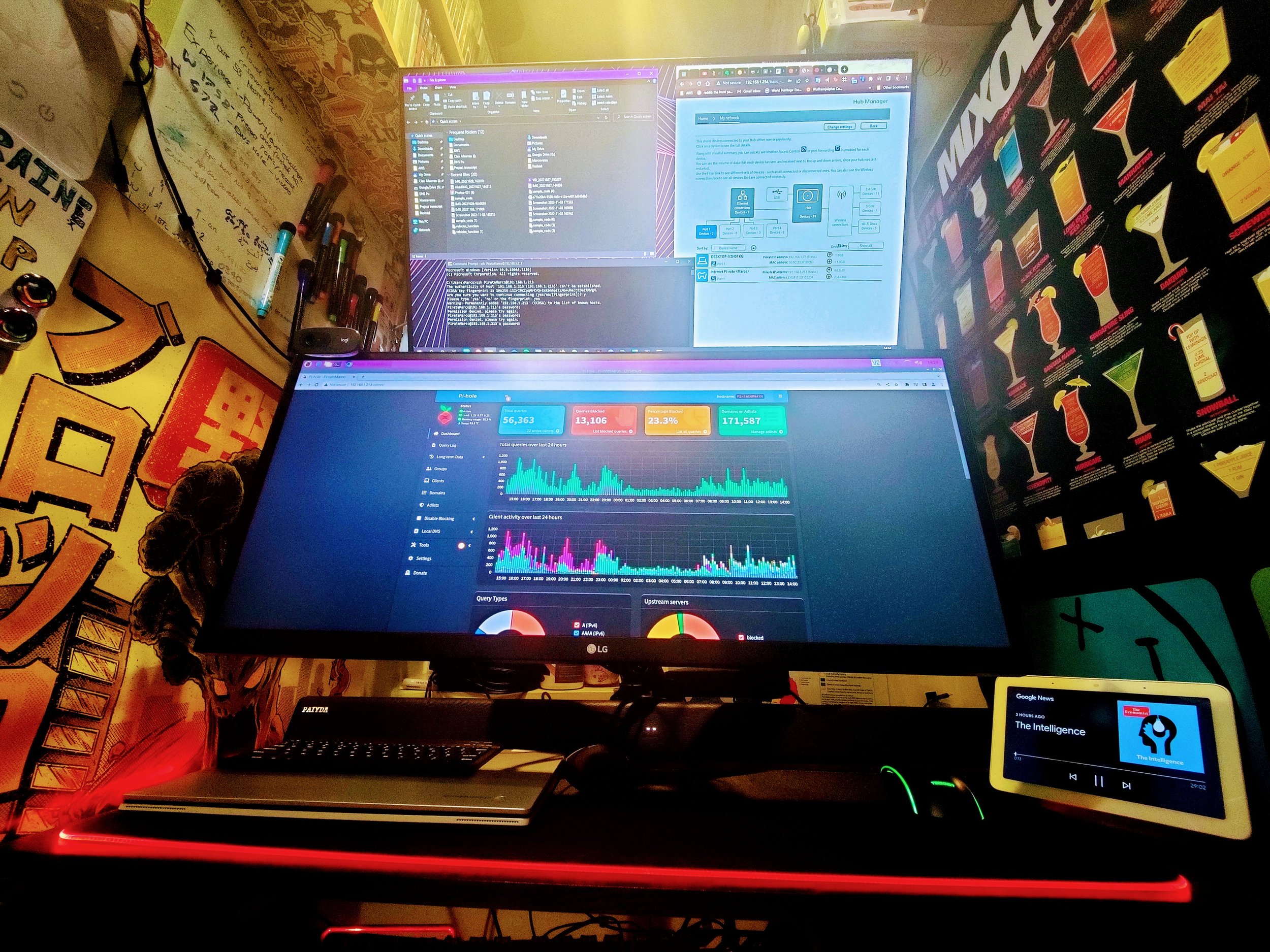
I now have a pi-hole server on my Raspberry Pi. Access has been granted to the admin interface along with the password to log into the admin account.
-
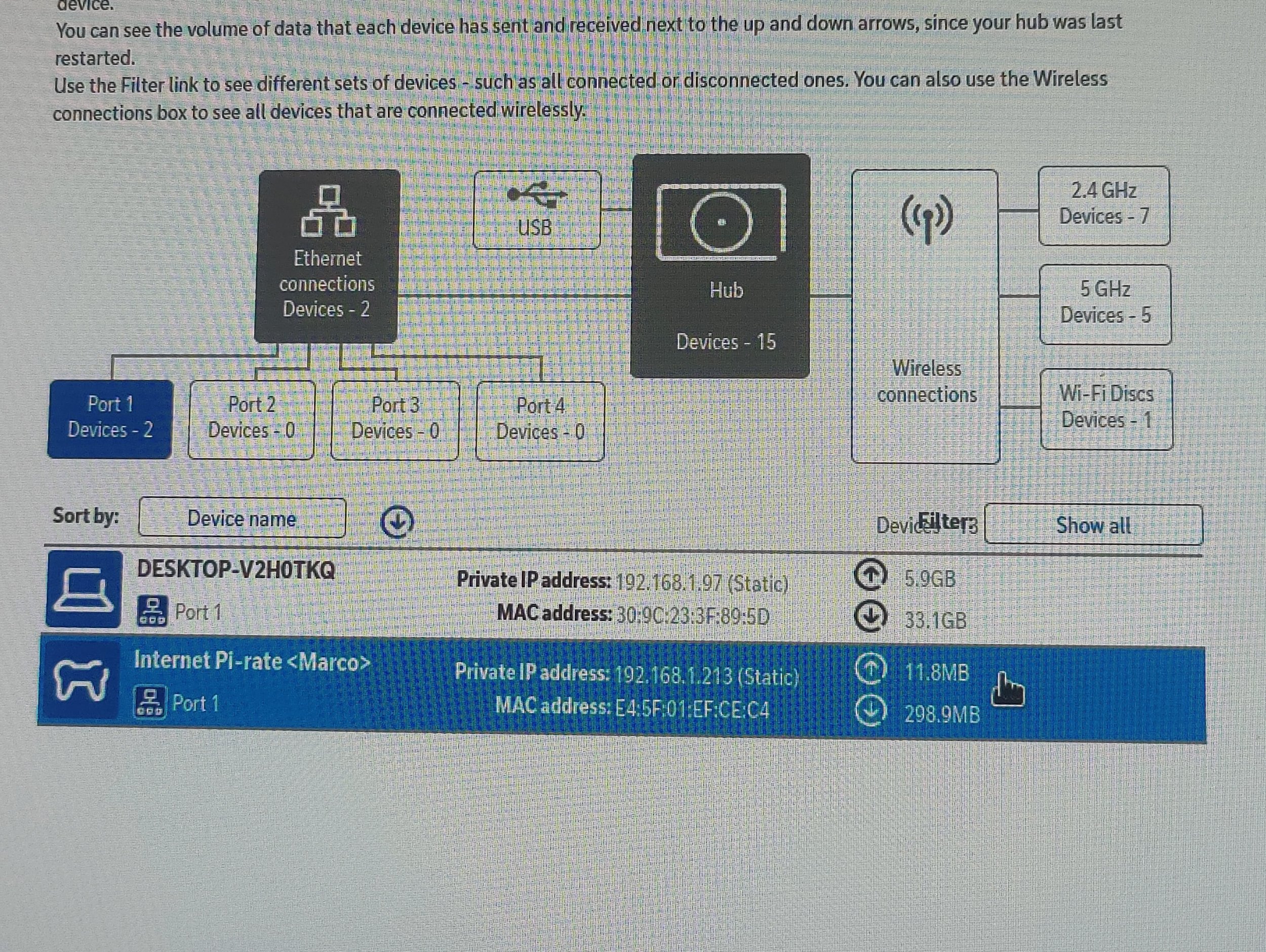
To get into the Pi-hole web interface, all I do is go to my private IP with the /admin suffix. In my case, http://192.168.1.213/admin
Logged in with the password and changed it to something more memorable
Enabled Query logs (Showing the most recent queries that have been made to the DNS server. An easy way to find the addresses which’ve been parsed by my router)
Whitelisting (Adding certain domain names to unblock sites by the DNS server. However, if that domain is blocked by a wildcard, it’ll remain blocked)
Blacklisting (The domain names which ought to be blocked by the DNS server)
Disable (Temporarily or permanently disable the functionality. It’ll continue to function as a normal DNS server, but on pause to see the on/off difference).
-
To enable pi-hole on a Router level so that it works on all devices automatically subscribed to my WLAN, I’d have to configure my router’s DHCP server’s default DNS settings.
Regrettably, this is an impossible task. My home wifi router (BT Hub 6) cosplays as the hands that drag one down to hell. Restrictions in place make a network-wide LAN impossible.
Instead, I’ve just changed the DNS setting for each of my devices. It’s a little more time-consuming, but works just as well.
For my Android devices, I navigate through settings > Wi-Fi > Wireless Networks > DNS > Entering the Raspberry Pi’s IP address
For my Windows Desktop: Control Panel > Network & sharing Center > Change Adapter Settings > IPv4 Networking TCP > Properties > Adjust DNS server resolution
Examples in action
Mobile devices- Sponsored ads blocked! When making product searches online (such as Raspberries on Pimoroni.co.uk - the site which I purchased the hardware from), it’s only possible to access their site through legitimate means.
Desktop devices - No more clutter on websites. Even scrubbing the scummiest of sites - such as the Daily Mail - the difference in performance & user experience is enormous. Sorry/not sorry, Rupert Murdoch!